Discovering the world of cybersecurity: an experience in CTF competition

Cybersecurity is a rapidly evolving field in computer science. Professionals and amateurs in this discipline must constantly study, research, and practice to stay on top of the latest techniques and vulnerabilities being discovered in an increasingly digitalized world. One way to stay in shape is by participating in a CTF (“Capture The Flag”) hacking competition, where participants put their skills to the test for fun, glory, and, sometimes, a bit of cash. In this article, I’ll briefly go over our experience participating in the CTF sponsored by GMV and hosted by the Sugus organization, created and run by students and graduates from the University of Valladolid’s School of Computer Science.
Our participation was possible largely thanks to our colleague Juan Álvarez-Ossorio, a cybersecurity professional at GMV with extensive experience in these kinds of competitions. It’s no secret that a large number of software developers and computer science engineers are tempted by the idea of venturing into the world of cybersecurity but are intimidated once they realize the sheer quantity and complexity of the information. Juan participated last year in the first edition together with other GMV colleagues, and ton this occasion, he encouraged Alberto Gentil and yours truly, Boris Treccani, to join the team that would be representing GMV this year. Given his experience in these kinds of activities, Juan become our coach and captain, putting together a series of resources and exercises that would help us prepare for the competition.
They spanned different areas, such as cryptography, forensic analysis, steganography, exploiting system vulnerabilities, memory manipulation, exploiting vulnerabilities in the web context both client-side and server-side, among others.
This training regimen started several months before the competition and we even ended up participating in a couple of online CTFs to become familiarized with the format of the competition and get used to managing time, since we had to achieve as much as possible within the limited timeframe of the competition, and therefore had to be comfortable working under pressure.
Participating in these online CTFs also gave us an idea of how far we had come with our training, though to be honest, they were open events with thousands of teams participating, and were much more advanced than what we were prepared for at the time.
We also started to prepare a page with resources and scripts we had used to solve the training exercises, with bits of code or notes we felt would be useful during the competition and that could save us a few valuable minutes, instead of trying to remember how to carry out the different processes on the fly. We were trying to create a toolbox that could potentially be helpful during the competition.
We also had to prepare the machines we would use to compete, installing software we might need for the challenges in the different categories. We needed programs for stenographic analysis of audio recordings, images and videos, text editors for scripting, install libraries that could be used for file analysis and handling, forensic analysis software, and several other tools we might need so we wouldn't waste time downloading them during the competition.
Once assigned to our table, we started to install our equipment and pay attention to the organizers’ directions and announcements. When the event began, we were provided with the credentials we needed to access the page with the descriptions of the challenges we had to solve.

Each challenge could be part of a specific field within cybersecurity or a combination of several disciplines, and each one had a description telling a brief story with hints or instructions that help you solve the problem. Points were assigned based on the difficulty of the challenge, and in the particular case of this CTF, the scoring system was dynamic, meaning that the value of a challenge was based on the number of teams who managed to solve it; the most teams were successful, the fewer points it was worth. Teams could exchange points for extra clues if they were stuck on a given challenge, but this isn’t usually a good idea, since it puts you at a disadvantage compared to the teams that solve the same challenge without resorting to this exchange for extra clues.
We started by briefly reading the description of each challenge to have a general idea of what we were facing and establish an order of priorities to earn the greatest number of points as quickly as possible.
There were cryptography challenges that were quite similar to the ones we had practiced and that we were able to solve almost instantly. For his part, Alberto set out to tackle a couple of challenges associated with the IoT (Internet of Things), which usually have to do with internet-connected devices. They're based on finding the vulnerability that allows you to establish a connection with the device and control it (in this case, surveillance cameras prepared by the event team that were hidden inside the campus, pointing to a blackboard with the answer phrase or flag that we had to enter in the answer field for the challenge to receive the point).
Meanwhile, Juan set out to solve the challenges in the fields of steganography, forensic analysis, reverse engineering and pwn, or binary exploitation (binaries are the executable files we all know and use, such as .exe and similar). Binary exploitation is a large and wide-ranging topic in cybersecurity, but it can be summarized as the act of obtaining and exploiting a vulnerability in a program in order to obtain data and privileges on the machine or modify the behavior of the program so that it will do what the attacker wants it to do.
It’s worth noting that these disciplines are not inherently malicious, as by studying and experimenting with how to breach existing systems, one can understand and design countermeasures to prevent or strengthen security in the event of attacks by malicious actors.
Going into the second hour of the competition, we were solving challenges at a good pace: Alberto with the IoT challenges, Juan with binary exploitation, and yours truly with cryptography challenges. Even so, for much of the competition there was a team constantly on our heels, and we couldn't let our guard down.
Even Juan, a seasoned veteran on this scene, was impressed by this team: whenever we got the answer to a challenge and gained some distance, they quickly caught up with us again. Basically, any poor decisions regarding time management or which of the available challenges to take on next could land us in second place.
At about the third-hour mark, we managed to secure several challenges that no one else had been able to solve, earning the maximum score for them and gaining a comfortable lead on second place, which is why we felt we had enough breathing room to attempt a few others that we thought might be bottomless rabbit holes.
Approaching the fourth-hour mark and by the end of the competition, we had managed to double the second-place score with 1500 points and secure first place.
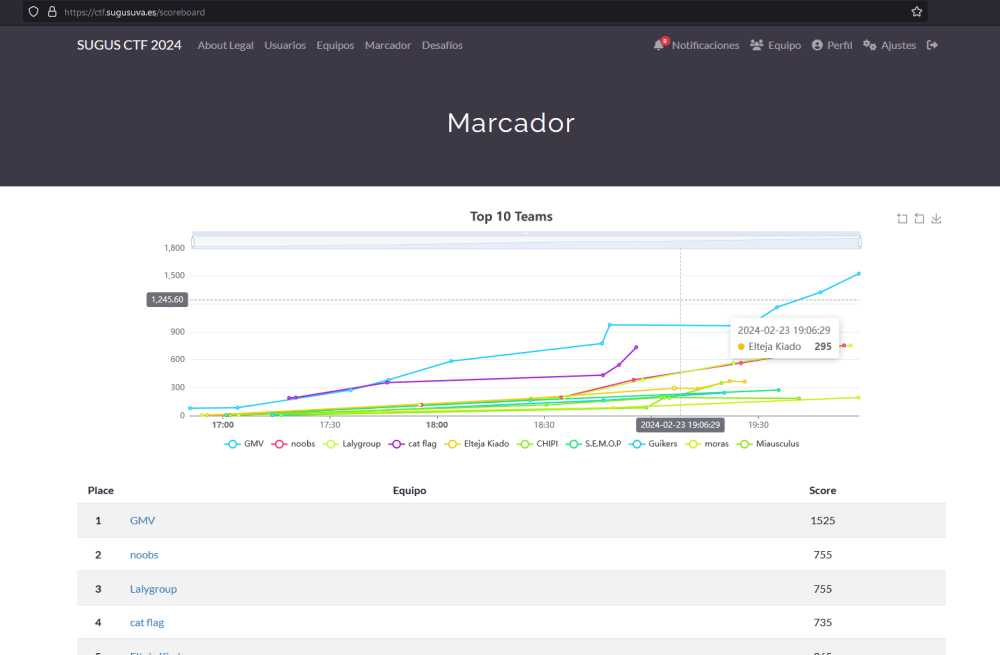
For me personally, winning the competition felt like getting off to a good start on a long journey. My colleagues were also pleased and proud with the results of so much hard work and all the time we had put in. In this case, the prize for the top finishers was a series of POP materials (pens, backpack, tote bag, stickers, UVA hoodies, etc,) and a certificate. The team that had been on our heels for much of the competition ended up in fourth place. In talking with them to find out what had happened, they told us that near the third-hour mark, one of the members was stuck trying to solve a challenge and instead of splitting up to try to solve other ones at the same time, the whole team focused on the problem that was vexing their member, and this decision cost them the podium.
It was a rewarding experience, teaching me that cybersecurity is a complex and vast world, but that nonetheless, with good planning, dedication, consistency, and a bit of guidance, it can easily become a feasible, rewarding, glamorous and exciting career.
In conclusion, I'd like to thank the Sugus organization and GMV for making this event possible, and I'd like to highlight the importance of companies such as GMV supporting these kinds of information technology competitions, which help support training and support the excellence of future professionals in these fields.
Author: Boris Pietro Treccani Gómez