IDPS: a perfect combination of machine learning and big data for protecting vehi-cles
As our cars become increasingly interconnected, mobility takes on a new meaning, offering new opportunities. The integration of new communications technologies in vehicles has generated an enormous variety of data from various communications sources.
A combination of Big Data and the headway being made in artificial intelligence (AI) is enabling us to handle data of all types from different sources, while also greatly simplifying real-time analysis.
AI and Big Data convergence is therefore playing a vital role in all industries, the automotive included.
GMV’s automotive business includes the development of new in-vehicle technology, including cybersecurity, an issue to which everyone has become much more sensitive in recent years.
For years now we at GMV have been studying new security protection techniques for internal and external vehicle communications.
Combining our Machine Learning and Big Data expertise, we have developed an Intrusion Detection and Prevention System (IDPS) based on algorithms that are trained up using machine learning techniques to make the detection of intrusions and anomalies (malicious attacks) much more effective and precise.
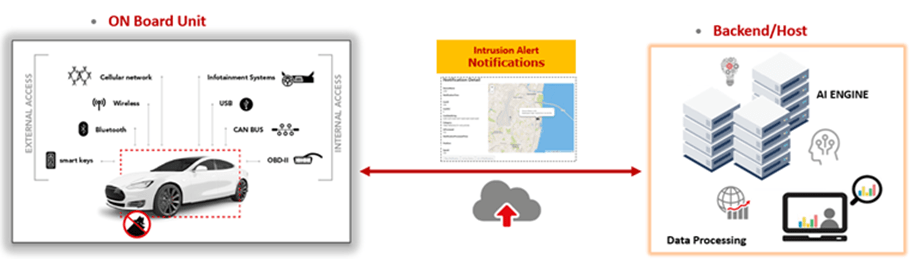
The general architecture of our IDPS is made up by several components:
- A telematic control unit (TCU) that collects the car’s data (CAN, Ethernet, USB data etc…) and performs a first and basic filter before sending the data on to a server. Within the TCU, therefore, simple rules would be applied, with a very low processing load, and hence easily integrated into any of the vehicle’s electronic units.
- The complementary part of the IDPS is an external server that receives the abovementioned filtered data and then uses smart algorithms to detect and classify anomalies/intrusions, flagging up alerts as need be. The cloud processing system means the in-vehicle processing load can be trimmed back; this in turn means much more complex intrusion detection methods can be used for any instances involving deep learning.
Our detection-algorithm design can be broken down into two main phases: training and anomaly detection.
In the offline training phase data packages are processed (CAN data packages, Ethernet packages, USB data) to extract a characteristic trait representing the network’s statistical behavior.
The labeling of each training package depends greatly on the machine-learning algorithms to be used. A simple example would be supervised learning: each training package has its binary label, i.e., a normal package or an abnormal or malicious package.
From the training data the algorithm learns how to allocate the output label to suit a new value, i.e., to predict the output value.
When unsupervised algorithms are being used, there is no labeled training data to go on. The algorithm therefore creates a series of data structures that can be cataloged in terms of resemblance and correlations, thus determining complex patterns and processes that will serve for identifying and classifying any anomalous behavior that might turn out to constitute an intrusion incident.
Our inhouse solution combines several machine-learning algorithms to be able to fine tune the intrusion detection procedure.
The efficiency and precision of the proposed model is assessed and validated by using real cases and data. From our own experience we have learned that the use of machine learning algorithms ensures rapid (down to milliseconds) anomaly-detection convergence, with a high rate of success and efficiency.
To complement intrusion detection there is the possibility of applying prevention methodologies; this is precisely why the complete solution is called an Intrusion Detection and Prevention System (IDPS).
The way prevention is phased into the system differs greatly according to the IDPS’s purpose and how it might affect vehicle and driver safety and security.
Normally, prevention tasks are broken down into active and passive actions.
Passive actions consist of a suspected-intrusion notification. Once the IDPS detects an intrusion, the user is sent a telematic notification, and the warning, which contains all the intrusion details, is then recorded in an internal database.
Active actions involve a series of measures to protect the vehicle or mitigate the threat it is exposed to. Depending on the criticality of the attack, this might be in real time and might have a big effect on the infected system.
We at GMV are convinced that the action to be taken in response to any suspected intrusion is crucial because it might impinge on vehicle safety: take the example of a simple blockage of the braking system’s CAN message, which might turn out to have fatal consequences.
For this reason we are now busily working away on the best security solution without ever losing sight of the safety aspects.
To be able to fine tune these models it is important to be able to work with a complete and bang up-to-date database for algorithm training and enhancing. Collaboration with OEMs and first-tier suppliers is very important too, in pursuit of these goals, to ensure they are offered the solution best suited to their needs. We therefore always work closely with them in the development of solutions of this type.
Author: Marco Donadio